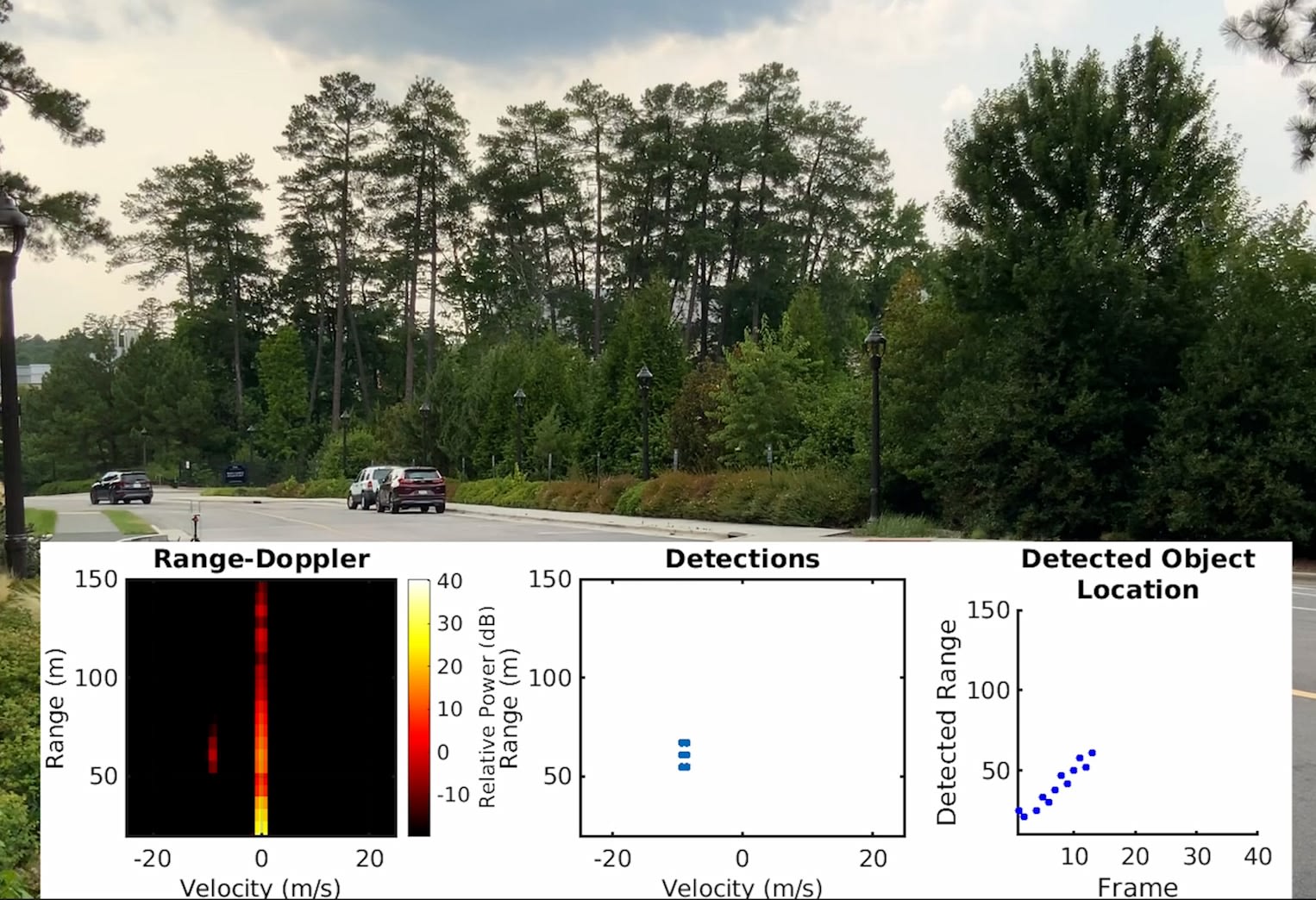
Engineers at Duke University have demonstrated a system they’ve dubbed MadRadar for fooling automotive radar sensors into believing almost anything is possible.
The technology can hide the approach of an existing car, create a phantom car where none exists, or even trick the radar into thinking a real car has quickly deviated from its actual course. Plus, it can do these things in the blink of an eye without having any prior knowledge about the specific settings of the victim’s radar, making it the most troublesome threat to radar security to date.
“Without knowing much about the targeted car’s radar system, we can make a fake vehicle appear out of nowhere or make an actual vehicle disappear in real-world experiments,” said Professor, Faculty Advisor, and Co-Author Miroslav Pajic. “We’re not building these systems to hurt anyone; we’re demonstrating the existing problems with current radar systems to show that we need to fundamentally change how we design them.”
In the MadRadar demonstration, the team showed off the capabilities of a radar-spoofing system they built. Each attack was done on real-world radar systems in actual cars moving at roadway speeds, the researchers said. It’s an impressive feat, given that if the spoofing radar signals are even a microsecond off the mark, the fake datapoint would be misplaced by the length of a football field.
“These lessons go far beyond radar systems in cars as well,” Pajic said. “If you want to build drones that can explore dark environments, like in search and rescue or reconnaissance operations, that don’t cost thousands of dollars, radar is the way to go.”
Here is an exclusive Tech Briefs interview — edited for length and clarity — with First Author David Hunt.
Tech Briefs: What was the biggest technical challenge you faced while developing MadRadar?
Hunt: I would say the biggest challenge was the levels of accuracy that are required when you estimate parameters. We are one of the first attacks that effectively don’t rely on previous knowledge of a radar’s settings. Previous attacks would essentially have had to know all that information to work. Ours is unique in that we learn these parameters simply by listening to the radio, like the radar’s radio waves.
One of the key parts here is you have to predict when the radar is going to transmit waves again. And because radio waves propagate at the speed of light, the timing constraints are incredibly difficult to meet. For example, if you are off by, say, 40 nanoseconds, a super small amount, your attack basically doesn’t land. So, to estimate these parameters to such a degree, was difficult.
Tech Briefs: Can you explain in simple terms how it works?
Hunt: At a high level, what radar does is it sends out radio waves into the environment. And, as you can imagine, they bounce off the environment and reflect back. Then, if you look at the time delay it takes for the wave to go out and come back, you can understand the range. If you plot their frequency over time, you can see it’s a linearly increasing slope. By changing the slope of that line and the time between chirps, you can adjust radar settings, basically. You can adjust the resolution it sees at the velocities that it can detect. So, what we do is learn the parameters. We listen to the radar waves and plot the frequency over time. That lets us see those chirps and learn their slopes and the time between them.
We have three different types of attacks. The first is we’re going to try to make the radar believe that there’s something there when there’s not. We’ll call that a false positive attack.
The second attack that we have is called a false negative attack. That is making a radar think that nothing is there when in fact there is something there. And then we can combine a false positive to add a fake object and a false negative to remove a real object. From the radar’s perspective, we’ve effectively moved the object. Those are the three attacks that we do.
Tech Briefs: The article says, ‘The researchers say MadRadar shows that manufacturers should immediately begin taking steps to better safeguard their products.’ If you were in their shoes, what steps would you take?
Hunt: First of all, the reason we like this work is to see why these systems are vulnerable. You want to design secure systems, but it’s more important to design secure systems against potentially feasible attacks. So, from the manufacturer side of things, even something as simple as randomizing your parameters every so often could be very useful in defending against attacks. For ours, if you subtly randomize your parameters, we can still detect that and launch a jamming attack. But if you, say, randomize your frame, the time you send out chirps, by a millisecond — from an attacker’s perspective — that can really change things.
Or, by changing the slope of your chirps a little bit so that you don’t really change the radar performance, but you prevent somebody from actually implementing a successful attack. It’s akin to when you get a Wi-Fi router — you change the password. Or, you change your computer passwords every so often.
But right when you’re designing these systems, you’re trying so hard to get ’em to work that security isn’t often at the forefront because who’s going to attack a commercial radar? A lot of times security is an afterthought. But working to understand how these attacks appear and if there are defenses in place — there are some that are fairly common that could be utilized if done right.
Tech Briefs: What are your next steps with regards to MadRadar? Do you have any other further plans/research/work/etc.?
Hunt: There are a lot of different things that we’re looking into. For this case, I’ll put two out there. In this work, we specifically focus on the range and velocity, which means that if we wanted to launch an attack against the radar, that could also detect the angle that things are at, we would have to be at the angle that the attack needed to be launched at. So, what we’re looking into now is, for example, is it possible to attack from the side of the road, but affect objects that are right in front of your car? Could we insert a point at a different angle or something like that?
We developed a simplified prototype using some software-defined radios. It was at a little bit of a lower frequency, a little bit limited capability. So, the second thing we’re doing now is we’re working toward ‘can we attack something at a more full-scale system?’ This requires a bit more processing capability, I would say, and more advanced hardware. So, we’re working to see what it looks like when it shows up in a real-world case on a full-scale system.
Beyond that, our lab is very focused on different security flaws. That’s understanding things like what are these attacks? What’s the biggest effect that these attacks can have? What happens if we compromise a radar? Can we design systems? We’re investigating things with multiple agent trusts. What if my measurements are compromised? Can we detect that you’ve been compromised and what specific vehicles were compromised?