The results of the first Pwn2Own security competition dedicated to automotive technology are in, and they make for sobering reading with vulnerabilities discovered in charging systems, in-car entertainment systems, and even the modem subsystem in Tesla electric vehicles.
The first Pwn2Own Automotive competition took place during the Automotive World conference in Tokyo, Japan this month. It took the highly successful Pwn2Own concept, which launched in 2007 and saw security researchers compete to find flaws in consumer products like laptops and smartphones with the promise of receiving both cash and the hardware they had “pwned” as a prize, and applied it to vehicles and related infrastructure — following their addition in 2019 as a valid target in the mainstream contest track.
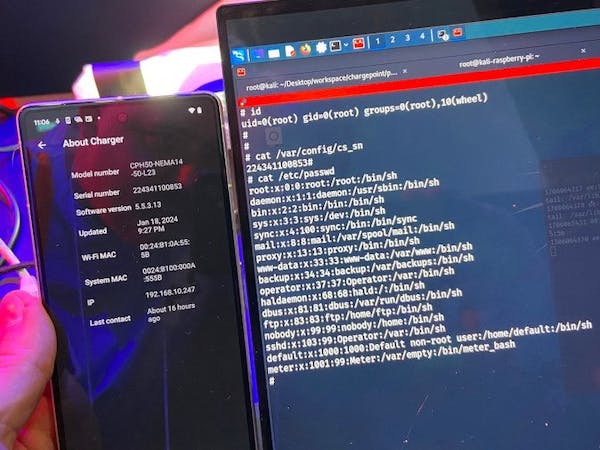
The first Pwn2Own Automotive contest has drawn to a close, with 49 vulnerabilities — including this flaw in Tesla’s modem subsystem. (📷: Synacktiv/Zero Day Initiative)
With the three-day challenge over, there’s little surprise to find that few products emerged unscathed. In the first day researchers demonstrated vulnerabilities in Automotive Grade Linux, ChargePoint, JuiceBox, Phoenix Contact, Ubiquiti Connect EV Station electric vehicle chargers, in-car entertainment systems from Alpine, Pioneer, and Sony, and the modem in Tesla vehicles — the latter providing root access.
On the second day, additional bugs were found in chargers from Autel and EMPORIA along with the previously-mentioned manufacturers. The third day saw more bugs found in the devices on test, bringing the total number of unique zero-day vulnerabilities to 49 — and resulting in Team Synacktiv receiving 50 “Master of Pwn” points and a grand prize total of $450,000 out of more than $1 million distributed among the competitors.
The contest targeted Tesla vehicle systems, in-car entertainment systems, and electric vehicle chargers. (📷: Midnight Blue/Zero Day Initiative)
Under the terms of the Pwn2Own Automotive contest details of the vulnerabilities disclosed are not released publicly following the close of the competition; instead, they become the property of the Zero Day Initiative (ZDI) and disclosed privately to each of the affected manufacturers — given them opportunity to patch the vulnerabilities before knowledge of how to exploit them becomes widespread.
More information on the contest participants and the vulnerabilities they found are available on the Zero Day Initiative blog.